Top 10 Types of Phishing Emails
Criminals have countless methods to trick email users.
 |
| By: David Ellis |
 This is achieved through a few different methods. Sometimes, cybercriminals trick email recipients into opening an email attachment that loads harmful malware onto their system. Other times, they trick recipients into providing sensitive personal information directly via web forms. Either way, these seemingly teeny mistakes could make serious ripples across your organization, compromising either corporate or personal security.
This is achieved through a few different methods. Sometimes, cybercriminals trick email recipients into opening an email attachment that loads harmful malware onto their system. Other times, they trick recipients into providing sensitive personal information directly via web forms. Either way, these seemingly teeny mistakes could make serious ripples across your organization, compromising either corporate or personal security.SEE ALSO: 7 Ways to Recognize a Phishing Email.
Typically, phishers send legitimate-looking emails that appear as though they originated from reputable companies that many people do business with like BestBuy, Amazon, Federal Express, DHL, and PayPal. The emails often ask customers to confirm information or to go to the business site by clicking on a provided link, and often include a statement of impending consequences if you fail to act.
Here are a few common ploys cybercriminals use to trick you.
1. The Government Maneuver
This type of email looks like it originated from a federal body, such as the FBI, and tries to scare you into providing your information. Common messages include, ‘Your insurance has been denied because of incomplete information. Click here to provide your information.’ Or, ‘Because you illegally downloaded files, your Internet access will be revoked until you enter the requested information in the form below.’2. The Friend Tactic
If an unknown individual claims to know you in an email, you are probably not suffering from amnesia. More than likely, it is an attempt to get you to wire him/her money. A variation on this theme is that one of your known friends is in a foreign country and needs your help. Before you send your ‘friend’ money, give them a call to verify. Your true friend’s email contact list was probably hijacked.3. The Billing Problem
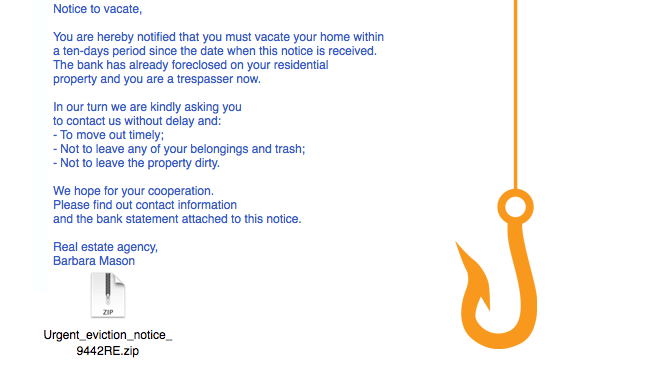
This phishing tactic is tricky because it appears quite legitimate. This email states that an item you purchased online cannot be shipped to you because the credit card was expired (or billing address wasn’t correct, etc.). If you click on the provided link, it takes you to a spoofed website and asks for updated payment/shipping information, etc.4. The Expiration Date
This type of email falsely explains that your account with [company name] is about to expire, and you must sign in as soon as possible to avoid losing all your data. Conveniently enough, there is a link in the email, which again takes you to a spoofed login page.5. The Virus Scare
This type of email states that your computer has been infected! In order to avoid losing your data and infecting your computer the email instructs you to follow the provided link, or download the “anti-virus” attachment.
 |
| Whatever you do, DON'T CLICK ON THE LINK! |
6. The Contest Winner
Don’t get too excited when you receive emails that claim you’ve won something, or received an inheritance from a relative you've never heard of. 99.9% of the time, these are absolutely bogus. To claim your prize, the email requires you click a link and enter your info for prize shipment.7. The Friendly Bank
Your bank may offer account notifications when certain amounts are withdrawn from your accounts. This ploy tricks you with a fake account notification stating that an amount has been withdrawn from your account that exceeds your notification limit. If you have any questions about this withdrawal (which you probably would), it gives you a convenient link that leads to a web form asking for your bank account number “for verification purposes.” Instead of clicking on the link, give your bank a call. They may want to take action on the malicious email. |
| Due to the graphics and opt-out instructions, this phishing attempt seems very legitimate. |
8. The Victim
Being wrongly accused of something doesn’t feel good. This type of phishing email acts as an angry customer whom supposedly sent you money in return for a shipped product. The email concludes with the threat that they will inform the authorities if they don’t hear from you. |
| This is another type of victim scam. Who wouldn't be a little worried after receiving this email? |
9. The Tax Communication
Practically everyone has annual taxes to submit. That’s why this phishing attempt is so popular. The message states that you are either eligible to receive a tax refund, or you have been selected to be audited. It then requests that you submit a tax refund request or tax form.10. The Checkup
This is one of the more unassuming phishing email attempts. It claims [company name] is conducting a routine security procedure and requests you verify your account by providing information. This scam is especially effective if you happen to be a customer of the named business.If you receive a phishing email:
- Don’t click on any links, open attachments, or expand any included pictures
- Don’t try to reply to the sender
- Report the scam (forward the e-mail to the FTC – spam@uce.gov)
- Delete the email from your computer
- If you do legitimate business with a company mentioned in the phishing email, you can call the business and ask if they would like you to forward the email to them, so they may take further action.
Was this post helpful? Share it!
David Ellis (GCIH, QSA, PFI, CISSP) is Director of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience. Check out his other blog posts.