Snapshot of HIPAA and Healthcare Data Security
Learn how healthcare professionals are handling HIPAA requirements.
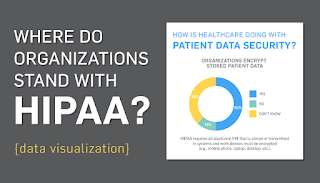 Many organizations likely realize it’s important to secure their patient data, but how many are actually doing it? We surveyed 42 healthcare professionals responsible for HIPAA compliance and discovered a few interesting things:
Many organizations likely realize it’s important to secure their patient data, but how many are actually doing it? We surveyed 42 healthcare professionals responsible for HIPAA compliance and discovered a few interesting things:- 38% don’t know if they encrypt stored patient data
- 37% require two-factor authentication for remote access
- 7% still share credentials for their EMR system
- 7% don’t have automatic timeouts/logouts on workstations
SEE ALSO: How Healthcare Security Complacency is Killing Your Organization
Data encryption
HIPAA requires all electronic PHI that is stored or transmitted in systems and work devices must be encrypted. This includes mobile phones, laptops, desktops, emails, EMRs, etc. Encrypting PHI essentially makes it useless to any potential hackers that manage to steal data. It’s an extra security layer that can’t be avoided.According to our survey, 50% of respondents encrypt data, 12% don’t, and 38% don’t know.That’s a little concerning, especially since encryption is a good way to secure your data.
SEE ALSO: Medical Data Encryption: Keeping Your PHI Secure
Two-factor Authentication
 Organizations that use remote access must implement two-factor authentication when logging into the data base. Two-factor authentication consists of needing to use two of the following items as credentials:
Organizations that use remote access must implement two-factor authentication when logging into the data base. Two-factor authentication consists of needing to use two of the following items as credentials:- Something you know (password, username, etc.)
- Something you have (code sent to phone)
- Something you are (finger print, biometrics)
Remember, the number one vulnerability attackers exploit in organizations is remote access. If you use it, make sure you’re using it securely.
SEE ALSO: Two Factor Authentication—Security Beyond Passwords
Unique ID credentials
All employees should have their own login IDs and passwords for computer, software, and physical access. This prevents hackers and social engineers from gaining access to sensitive data through easy means.The organizations we interviewed are doing fairly well with this requirement as only 7% share credentials. This is promising since it has been a problem in the past.
Need help with getting HIPAA compliant? Let’s see what you need to do.
 Automatic timeouts/logouts on workstations
Automatic timeouts/logouts on workstations
All workstations should have an automated timeout/logout on computers and devices (e.g., a password-protected screensaver pops up on a computer after a set amount of time). This helps discourage social engineers from trying to access data from these workstations when employees aren’t there.
Similarly, our surveyed healthcare professionals are doing really well with this requirement with 90% having these timeouts/logouts enabled, and only 7% not having them.
SEE ALSO: Healthcare Reception Desks: Breeding Ground for HIPAA Compromise
So how are we doing?
While organizations seem to be doing better in some elements of HIPAA, there’s still room for improvement. Remote access security and data encryption still remain big problems, ones that many of our interviewed healthcare professionals either aren’t addressing, or have employees unaware of them. Both are equally disturbing outcomes.When it comes to HIPAA, you need to make sure your organization is compliant with all security requirements. If you don’t, you leave your organization vulnerable to attackers. Keep your data safe!
Check out our data visualization on HIPAA data security: How is Healthcare Doing with Patient Data Security?

